- May 31, 2023
- Posted by: Surender Kumar
- Category: PowerShell
Remove secrets from AWS secrets manager with PowerShell
Table of Contents
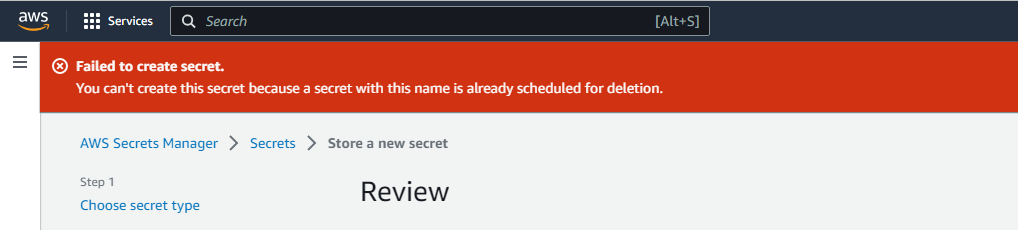
Recently, I wrote a post on how to securely store secrets in AWS secrets manager. If you are already using the Secrets Manager, you might come across the following error:
You can’t create this secret because a secret with this name is already scheduled for deletion
Cause of error
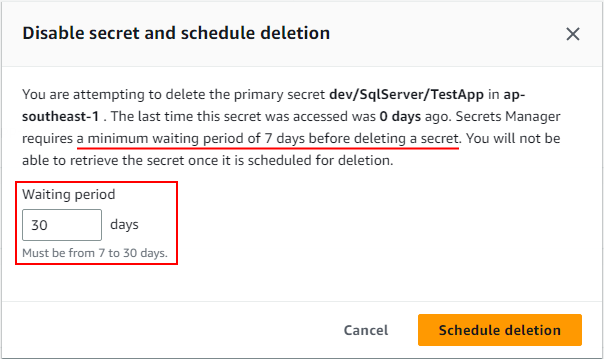
The reason of this error is quite obvious. When you delete a secret from AWS secrets manager, it is not immediately deleted, by default. Instead, it is marked for deletion and gets deleted automatically after 30 days. When deleting a secret using AWS console, you can reduce the deletion time to minimum 7 days but there is no way to delete it permanently, immediately.
Now the problem is that, once you have a secret marked for deletion, you will not be able to create a new secret with the same name since it already exists in the secrets manager. A simple workaround is to use a slightly different name. But what if your organizational requirement forces you to use the exact same name?
How to fix
A simple fix of error is to use PowerShell to permanently remove the secret without marking it for deletion. To do that, launch a PowerShell console and make sure you have installed AWS PowerShell module and setup your AWS profile as discussed here.
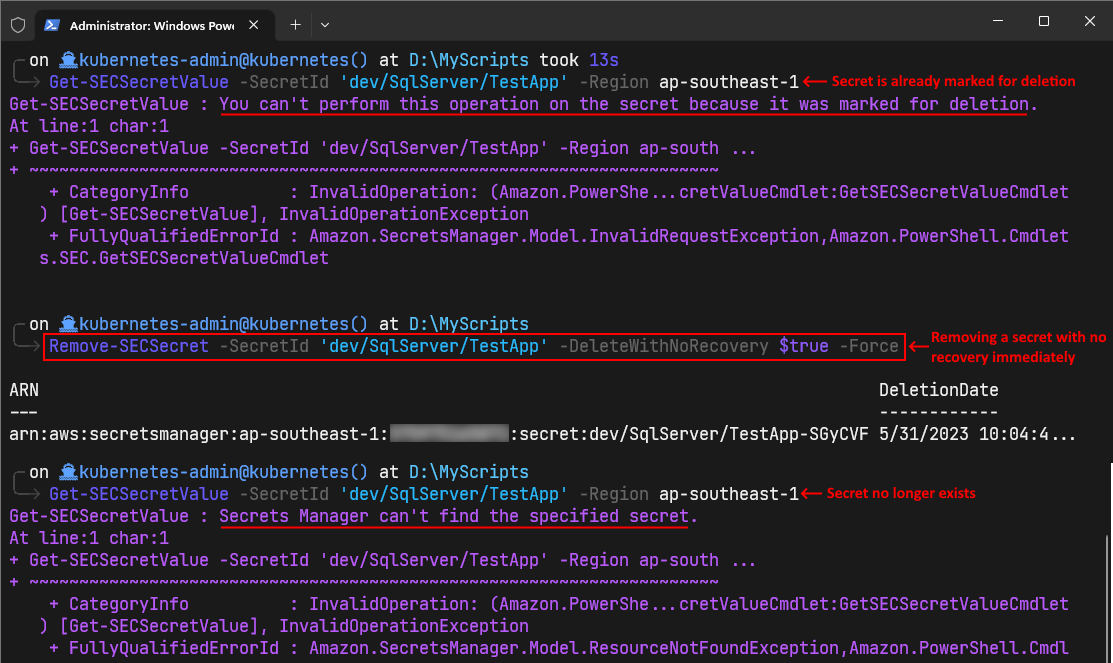
- To view a secret value, use the Get-SECSecretValue command as shown below:
Get-SECSecretValue -SecretId 'dev/SqlServer/TestApp' -Region ap-southeast-1
Don’t forget to specify your own secret with -SecretId parameter.
- To permanently remove the secret, use the Remove-SECSecret command as shown below:
Remove-SECSecret -SecretId 'dev/SqlServer/TestApp' -DeleteWithNoRecovery $true -Force
You can see in the above screenshot, when we ran the Get-SECSecretValue command first, it reported that the secret is marked for deletion. The Remove-SECSecret command with -DeleteWithNoRecovery parameter removed the secret permanently so you can now go ahead and create a new secret with the same name. That was it for this post.