- July 14, 2015
- Posted by: Surender Kumar
- Category: Cisco Switches
Network Traffic Analysis Using Cisco Switch
Table of Contents
In this section we will discuss about Switched Port Analyzer (SPAN), a feature of Catalyst series switches which helps you to capture network traffic for Network Traffic Analysis. The SPAN is sometimes also known as port mirroring or port monitoring, selects network traffic for analysis by a network analyzer. The network analyzer can be a Cisco SwitchProbe device or other Remote Monitoring (RMON) probe.
SPAN is supported by wide range of Cisco catalyst switches like Catalyst Express 500, 6000, 5000, 4900, 4500, 3750, 3560, 3550, 2960 series.
Background Information
The SPAN feature was introduced on switches because of a fundamental difference between switches and hubs. When a hub receives a packet on one port, it broadcast out that packet on all ports except the source port. But when a switch is powered on, it starts building up a Layer 2 forwarding table on the basis of the source MAC address of the different packets that the switch receives. After this forwarding table is built, the switch forwards traffic that is destined for a MAC address directly to the corresponding port. So, the switch is known for its point-to-point switching strategy and Hub is known for broadcast.
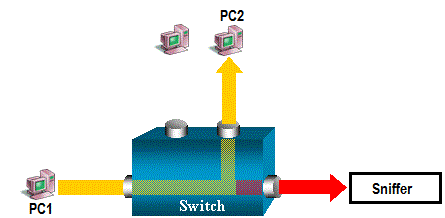
Consider the following scenario, if you want to capture network traffic that is sent by PC1 to PC2, and both are connected to a Hub, just attach a sniffer on any port of Hub. All other ports can see the traffic of PC1 and PC2:
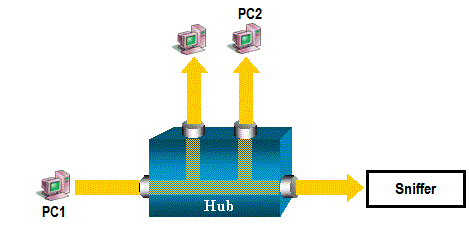 Now, Let’s replace the Hub with a Switch. On a switch, after Switch learns MAC address of the PC2, the traffic from PC1 to PC2 is only forwarded to the PC2 port and no other port can see the traffic. Therefore, the sniffer can not capture all the traffic:
Now, Let’s replace the Hub with a Switch. On a switch, after Switch learns MAC address of the PC2, the traffic from PC1 to PC2 is only forwarded to the PC2 port and no other port can see the traffic. Therefore, the sniffer can not capture all the traffic:
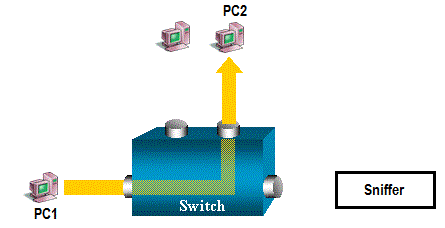 The sniffer will only capture broadcast or muticast traffic.
The sniffer will only capture broadcast or muticast traffic.
But what if you want to capture all the traffic?
This can be done by configuring SPAN on Switch. After SPAN is configured, the Switch will send a copy of every frame to destination port where sniffer is attached.
SPAN Terminology
- Ingress traffic: Traffic that enters the switch.
- Egress traffic: Traffic that exits out of the switch.
- Source (SPAN) port: A port that is monitored using SPAN feature.
- Source (SPAN) VLAN: When the traffic of complete VLAN is monitored using SPAN, the VLAN is known as Source (SPAN) VLAN.
- Destination (SPAN) port: A port that monitors source ports, usually where Sniffer is attached. It is also known as Monitor port.
- Reflector Port: A port that copies packets onto an Remote SPAN VLAN.
- Local SPAN: The SPAN feature is local when the monitored ports are all located on the same switch as the destination port.
- Remote SPAN (RSPAN): RSPAN is used when source ports are not located on the same switch as the destination port. RSPAN is an advanced feature that requires a special VLAN to carry the traffic that is monitored by SPAN between switches. It is not supported on all switches.
- Port-based SPAN (PSPAN): The user specifies one or several source ports on the switch and one destination port.
- VLAN-based SPAN (VSPAN): It is used when all the ports belonging to a particular VLAN are monitored.
- Administrative source: A list of source ports or VLANs that have been configured to be monitored.
- Operational source: A list of ports that are effectively monitored. This list of ports can be different from the administrative source. For example, a port that is in shutdown mode can appear in the administrative source, but is not effectively monitored.
Characteristics of Source Port
A source port, also called a monitored port, is a switched or routed port that you monitor for traffic analysis. In a single local SPAN session or RSPAN source session, you can monitor source port traffic, such as received (Rx), transmitted (Tx), or bidirectional (both). The switch supports any number of source ports (up to the maximum number of available ports on the switch) and any number of source VLANs.
A source port has following characteristics:
- It can be any port type, such as EtherChannel, FastEthernet, GigabitEthernet etc.
- It can be monitored in multiple SPAN sessions.
- It cannot be a destination port.
- Each source port can be configured with a direction (ingress, egress, or both) to monitor. For EtherChannel sources, the monitored direction applies to all physical ports in the group.
- Source ports can be in the same or different VLANs.
- For VLAN SPAN sources, all active ports in the source VLAN are included as source ports.
When you monitor a trunk port as a source port, all VLANs active on the trunk are monitored by default. You can use VLAN filtering in order to limit SPAN traffic monitoring on trunk source ports to specific VLANs.
Characteristics of Source VLAN
VSPAN is the monitoring of the network traffic in one or more VLANs. The SPAN or RSPAN source interface in VSPAN is a VLAN ID, and traffic is monitored on all the ports for that VLAN.
VSPAN has following characteristics:
- All active ports in the source VLAN are included as source ports and can be monitored in either or both directions.
- On a given port, only traffic on the monitored VLAN is sent to the destination port.
- If a destination port belongs to a source VLAN, it is excluded from the source list and is not monitored.
- If ports are added to or removed from the source VLANs, the traffic on the source VLAN received by those ports is added to or removed from the sources that are monitored.
- You cannot use filter VLANs in the same session with VLAN sources.
- You can monitor only Ethernet VLANs.
Characteristics of Destination Port
Each local SPAN session or RSPAN destination session must have a destination port or monitor port that receives a copy of traffic from the source ports and VLANs.
A destination port has following characteristics:
- For local SPAN session, a destination port must reside on the same switch as the source port.
- A destination port can be any Ethernet physical port.
- A destination port can participate in only one SPAN session at a time.
- A destination port cannot be a source port.
- A destination port cannot be an EtherChannel group.
- A destination port can be a physical port that is assigned to an EtherChannel group, even if the EtherChannel group has been specified as a SPAN source. The port is removed from the group while it is configured as a SPAN destination port.
- The port does not transmit any traffic except that traffic required for the SPAN session unless learning is enabled. If learning is enabled, the port also transmits traffic directed to hosts that have been learned on the destination port.
- The state of the destination port is up/down by design. The interface shows the port in this state in order to make it evident that the port is currently not usable as a production port.
- If ingress traffic forwarding is enabled for a network security device. The destination port forwards traffic at Layer 2.
- A destination port does not participate in any of the Layer 2 protocols (STP, VTP, CDP, DTP, PagP).
- A destination port that belongs to a source VLAN of any SPAN session is excluded from the source list and is not monitored.
- A destination port receives copies of sent and received traffic for all monitored source ports. If a destination port is oversubscribed, it can become congested. This congestion can affect traffic forwarding on one or more of the source ports.
Characteristics of Reflector Port
The reflector port is the mechanism that copy frames onto an RSPAN VLAN. The reflector port forwards only the traffic from the RSPAN source session with which it is affiliated. Any device connected to a port set as a reflector port loses connectivity until the RSPAN source session is disabled.
The reflector port has these characteristics:
- It is a port set to loopback.
- It cannot be an EtherChannel group or trunk.
- It can be a physical port that is assigned to an EtherChannel group, even if the EtherChannel group is specified as a SPAN source. The port is removed from the group while it is configured as a reflector port.
- A port used as a reflector port cannot be a SPAN source or destination port, nor can a port be a reflector port for more than one session at a time.
- It is invisible to all VLANs.
- The native VLAN for looped-back traffic on a reflector port is the RSPAN VLAN.
- The reflector port loops back untagged traffic to the switch. The traffic is then placed on the RSPAN VLAN and flooded to any trunk ports that carry the RSPAN VLAN.
- Spanning tree is automatically disabled on a reflector port.
- A reflector port receives copies of sent and received traffic for all monitored source ports.
Well! This is enough of explanation. Now, let’s go ahead into configuration.
SPAN on the Catalyst 2940, 2950, 2960, 2970, 3550, 3560, 3750 Series Switches
Things to remember while configuring SPAN on above said switch models.
- The Catalyst 2950 Switches can have only one SPAN session active at a time and can monitor only source ports. These switches cannot monitor VLANs.
- The Catalyst 2950 and 3550 Switches can forward traffic on a destination SPAN port in Cisco IOS Software Release 12.1(13)EA1 and later.
- The Catalyst 3550, 3560, and 3750 Switches can support up to two SPAN sessions at a time and can monitor source ports as well as VLANs.
- The Catalyst 2970, 3560, and 3750 Switches do not require the configuration of a reflector port when you configure an RSPAN session.
- The Catalyst 3750 Switches support session configuration with the use of source and destination ports that reside on any of the switch stack members.
- Only one destination port is allowed per SPAN session, and the same port cannot be a destination port for multiple SPAN sessions. Therefore, you cannot have two SPAN sessions that use the same destination port.
Local SPAN:
C2960#conf t Enter configuration commands, one per line. End with CNTL/Z. C2960(config)#monitor session 1 source interface fastethernet 0/1 C2960(config)#monitor session 1 destination interface fastethernet 0/10 C2960#show monitor session 1 Session 1--------- Source Ports: RX Only: None TX Only: None Both: Fa0/1 Destination Ports: Fa0/10 C2960#
In above configuration steps, I have configured local SPAN session 1 on Catalyst 2960 switch. The monitor session 1 source interface command creates SPAN session 1 on switch with source port fastEthernet0/1 and monitor session 1 destination interface command sets the destination port for SPAN session. You can use show monitor session command to view the SPAN configuration on switch.
Now, let’s configure Remote SPAN.
Remote SPAN:
In order to monitor traffic for a particular VLAN that resides in two switches directly connected, configure these commands on the switch that has the destination port. In this example, we will monitor the traffic from VLAN 10 that is spread across two switches:
On the Switch1, use the following configuration command:
C3750-SW1#config term
C3750-SW1(config)#monitor session 1 destination remote vlan 10
C3750-SW1(config)#end
On Switch2, use the following configuration commands to configure source VLAN and destination port.
C3750-SW2#config term C3750-SW2(config)#monitor session 1 source vlan 10 C3750-SW2(config)#monitor session 1 destination interface fastethernet 0/10 C3750-SW2(config)#end C3750-SW2#
You can connect a host running any Network Traffic Analysis software like Capsa from colasoft or Solarwinds NetFlow Traffic Analyzer on SPAN destination port. You need not to configure any TCP/IP on the host and the host can not be used for other production purpose. Below, I have given a snippet of Traffic capturing using Capsa.
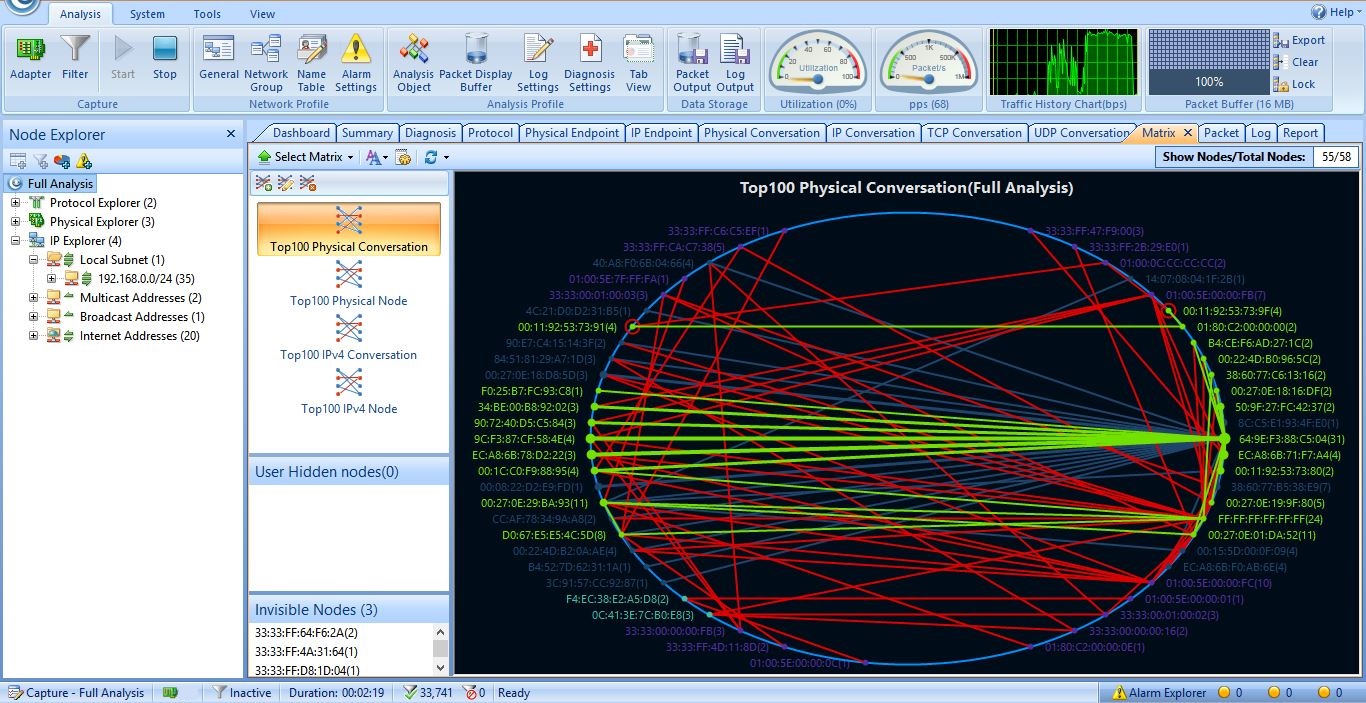 This concludes the Network Traffic Analysis section and SPAN configuration.
This concludes the Network Traffic Analysis section and SPAN configuration.