- July 17, 2015
- Posted by: Surender Kumar
- Category: Cisco Routers
Site to Site IPsec VPN Tunnel
Table of Contents
A virtual private network (VPN) is a technology that creates an encrypted connection between two or more devices or Local Area Networks by using public networks such as internet.
There are mainly two types of VPN connections:
- Remote Access VPN: This is user-to-LAN VPN connection used when employees of a company who are in remote locations and need to connect to the company’s private network.
- Site-to-Site VPN: This VPN allows offices in multiple remote locations to establish secure connection to each other over a public network such as the Internet. Site-to-site VPN extends the company’s network, making computer resources from one location available to the people at other locations.
There may be other types of VPN connections as well but in this section, I will discuss Site-to-Site VPN. Being a Networking professional, you should know how to configure site to site VPN.
We will configure a site-to-site VPN tunnel between two Cisco routers with static public IP addresses. The traffic betwwen them is protected with IPsec (Internet Protocol Security). So, both of the remote offices can communicate using internet via secure tunnel.
Before going into configuration, I would like to discuss about ISAKMP (Internet Security Association and Key Management Protocol). Both ISAKMP and IPsec are considered as the building blocks of VPN tunnel. ISAKMP protocol is a part of IKE (Internet Key Exchange) which is used to establish framework authentication and key exchange. ISAKMP negotiation is done in two phases: Phase 1 and Phase 2.
In Phase 1, a tunnel is created to protect ISAKMP negotiation messages. In Phase 2, a tunnel is created to protect data. Then IPSec encrypts the data using encryption algorithms.
Consider the following network diagram. We have two offices at different locations connected to internet by router Site-1 and Site-2.
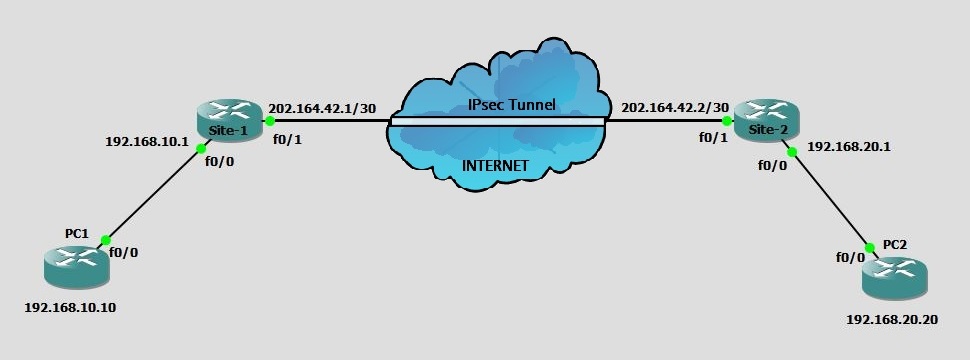
Site-1 is connected to a LAN 192.168.10.0/24 and Site-2 is connected to another LAN 192.168.20.0/24. You have to connect two offices securely to allow the full communication between LANs.
Firstly, I will configure both Site-1 and Site-2 routers so that both can ping each other. We are assuming that they are connected to internet with static public IPs. So, they must reach each other without any additional configuration.
On Site-1 Router:
Router#conf t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#hostname Site-1 Site-1(config)#int fa0/0 Site-1(config-if)#ip address 192.168.10.1 255.255.255.0 Site-1(config-if)#no shutdown Site-1(config-if)#int fa0/1 Site-1(config-if)#ip add 202.164.42.1 255.255.255.252 Site-1(config-if)#no shutdown Site-1(config-if)#end Site-1#
On Site-2 Router:
Router#conf t Enter configuration commands, one per line. End with CNTL/Z. Router(config)#hostname Site-2 Site-2(config)#int fa0/0 Site-2(config-if)#ip add 192.168.20.1 255.255.255.0 Site-2(config-if)#no shut Site-2(config-if)#int fa0/1 Site-2(config-if)#ip add 202.164.42.2 255.255.255.252 Site-2(config-if)#no shut Site-2(config-if)#^Z Site-2#
Now, both router should ping each other.
Site-1#ping 202.164.42.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 202.164.42.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/58/68 ms
Site-1#
Site-1 Router Configuration
Configuring ISAKMP (Phase-1)
I am going to create ISAKMP Phase-1 policy on Site-1 router.
Site-1#conf t Enter configuration commands, one per line. End with CNTL/Z. Site-1(config)#crypto isakmp policy 1 Site-1(config-isakmp)#encryption ? 3des Three key triple DES aes AES - Advanced Encryption Standard. des DES - Data Encryption Standard (56 bit keys). Site-1(config-isakmp)#encryption 3des Site-1(config-isakmp)#hash ? md5 Message Digest 5 sha Secure Hash Standard Site-1(config-isakmp)#hash md5 Site-1(config-isakmp)#group 2 Site-1(config-isakmp)#lifetime ? <60-86400> lifetime in seconds Site-1(config-isakmp)#lifetime 86400 Site-1(config-isakmp)#authentication pre-share Site-1(config-isakmp)#exit
In above configuration,
encryption 3des – The encryption method to be used for Phase 1.
hash md5 – The hashing algorithm used is message digest 5.
group 2 – This is Diffie-Hellman group to be used.
lifetime 86400 – This is session lifetime expressed in seconds. 86400 is the default value.
authentication pre-share – To use preshared key (password) for authentication.
You need to create multiple ISAKMP policies as we have create policy 1 above, if you are connecting to multiple sites from this router.
Now we have to specify the pre-shared key (password) used for authentication.
Site-1#conf t
Site-1(config)#crypto isakmp key Abc@123 address 202.164.42.2
Site-1(config)#
The password (Abc@123) must match on both routers for successful negotiation and the address given here is the public IP address of Site-2 router.
Next, we have to configure IPsec. I will create an extended access-list so that only the interesting traffic (traffic destined towards Site-2 LAN) should be sent through VPN tunnel.
Site-1(config)#ip access-list extended VPN-Traffic Site-1(config-ext-nacl)#permit ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 Site-1(config-ext-nacl)#end Site-1#
VPN-Traffic is our named ACL which will categorize traffic sourced from 192.168.10.0 /24 subnet and destined towards 192.168.20.0 /24 subnet. Only this traffic should be considered as interseting traffic which will be sent over VPN tunnel.
Configuring ISAKMP (Phase-2)
Here we will create IPsec transform set which will be used to encrypt the data flowing through tunnel. Then we will create a crypto map which will join IPsec and ISAKMP policy together.
Site-1#conf t Enter configuration commands, one per line. End with CNTL/Z. Site-1(config)#crypto ipsec transform-set SET1 ? ah-md5-hmac AH-HMAC-MD5 transform ah-sha-hmac AH-HMAC-SHA transform comp-lzs IP Compression using the LZS compression algorithm esp-3des ESP transform using 3DES(EDE) cipher (168 bits) esp-aes ESP transform using AES cipher esp-des ESP transform using DES cipher (56 bits) esp-md5-hmac ESP transform using HMAC-MD5 auth esp-null ESP transform w/o cipher esp-seal ESP transform using SEAL cipher (160 bits) esp-sha-hmac ESP transform using HMAC-SHA auth Site-1(config)#crypto ipsec transform-set SET1 esp-3des ? ah-md5-hmac AH-HMAC-MD5 transform ah-sha-hmac AH-HMAC-SHA transform comp-lzs IP Compression using the LZS compression algorithm esp-md5-hmac ESP transform using HMAC-MD5 auth esp-sha-hmac ESP transform using HMAC-SHA auth <cr> Site-1(config)#crypto ipsec transform-set SET1 esp-3des esp-md5-hmac Site-1(cfg-crypto-trans)#exit Site-1(config)#crypto map MAP ? <1-65535> Sequence to insert into crypto map entry client Specify client configuration settings isakmp Specify isakmp configuration settings isakmp-profile Specify isakmp profile to use local-address Interface to use for local address for this crypto map redundancy High availability options for this map Site-1(config)#crypto map MAP 10 ? ipsec-isakmp IPSEC w/ISAKMP ipsec-manual IPSEC w/manual keying <cr> Site-1(config)#crypto map MAP 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. Site-1(config-crypto-map)#set peer 202.164.42.2 Site-1(config-crypto-map)#set ? identity Identity restriction. ip Interface Internet Protocol config commands isakmp-profile Specify isakmp Profile nat Set NAT translation peer Allowed Encryption/Decryption peer. pfs Specify pfs settings security-association Security association parameters transform-set Specify list of transform sets in priority order Site-1(config-crypto-map)#set transform-set SET1 Site-1(config-crypto-map)#match address VPN-Traffic Site-1(config-crypto-map)#end Site-1#
Under crypto map configuration, I have used set peer 202.164.42.2 command to specify the destination (Site-2) router’s public IP address and set transform-set SET1 command to specify the transform-set to be used. The match address VPN-Traffic command is used to specify the name of extended ACL created to identify the interesting traffic.
Now, it is time to apply the crypto-map to outside interface (which is connected to ISP) which is interface fastEthernet0/1 in our network. You can apply only one crypto-map per interface.
Site-1#conf t Enter configuration commands, one per line. End with CNTL/Z. Site-1(config)#int fa0/1 Site-1(config-if)#crypto map MAP *Jul 17 13:33:48.571: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON Site-1(config-if)#end Site-1#
Notice that once crypto-map is applied on interface, you will receive a message “ISAKMP is ON”.
Network Address Translation (NAT) Configuration
Network Address Translation (NAT) is needed to be configured on Site-1 as well Site-2 router to provide Internet access to PCs on different portions of LAN. This can be done by using another extended ACL on the router and this ACL will prevent the interesting traffic not to be translated, means the traffic sourced from 192.168.10.0/24 subnet and destined towards 192.168.20.0/24 subnet will not undergo NAT operation. I’ve already said that NAT is required to allow internet access on PCs.
Site-1#conf t Enter configuration commands, one per line. End with CNTL/Z. Site-1(config)#ip access-list extended NO-NAT Site-1(config-ext-nacl)#deny ip 192.168.10.0 0.0.0.255 192.168.20.0 0.0.0.255 Site-1(config-ext-nacl)#permit ip 192.168.10.0 0.0.0.255 any Site-1(config-ext-nacl)#exit Site-1(config)#ip nat inside source list NO-NAT interface fastEthernet 0/1 overload Site-1(config)#int fa0/0 Site-1(config-if)#ip nat inside Site-1(config-if)#int fa0/1 Site-1(config-if)#ip nat outside Site-1(config-if)#^Z Site-1#
In above steps, I have configured and enabled Port Address Translation (NAT overload). If you have no idea about NAT, you can take a look at this section.
SIte-1 is now configured. Now I will go to Site-2 router and do the same configuration. The only difference will be public IP address of Site-1 router. Also the source and destination in ACLs will be flipped.
Site-2 Router Configuration
I have given the complete configuration of Site-2 router below:
Site-2#config t Enter configuration commands, one per line. End with CNTL/Z. Site-2(config)#crypto isakmp policy 1 Site-2(config-isakmp)#hash md5 Site-2(config-isakmp)#encryption 3des Site-2(config-isakmp)#group 2 Site-2(config-isakmp)#lifetime 86400 Site-2(config-isakmp)#authentication pre-share Site-2(config-isakmp)#crypto isakmp key Abc@123 address 202.164.42.1 Site-2(config)#ip access-list extended VPN-Traffic Site-2(config-ext-nacl)#permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 Site-2(config-ext-nacl)# Site-2(config-ext-nacl)#crypto ipsec transform-set SET1 esp-3des esp-md5-hmac Site-2(cfg-crypto-trans)#crypto map MAP 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. Site-2(config-crypto-map)#set peer 202.164.42.1 Site-2(config-crypto-map)#set transform-set SET1 Site-2(config-crypto-map)#match address VPN-Traffic Site-2(config-crypto-map)#int fa0/1 Site-2(config-if)#crypto map MAP *Jul 17 14:01:57.707: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON Site-2(config-if)#ip access-list extended NO-NAT Site-2(config-ext-nacl)#deny ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 Site-2(config-ext-nacl)#permit ip 192.168.20.0 0.0.0.255 any Site-2(config-ext-nacl)#exit Site-2(config)#ip nat inside source list NO-NAT interface fastEthernet 0/1 overload Site-2(config)#int fa0/0 Site-2(config-if)#ip nat inside Site-2(config-if)#int fa0/1 Site-2(config-if)#ip nat outside Site-2(config-if)#end Site-2#
VPN tunnel is now configured.
Verify the IPsec VPN Tunnel
You can view the status of security association (SA) using show crypto isakmp sa command and complete IPsec policy details using show crypto ipsec sa command.
Site-1#show crypto isakmp sa dst src state conn-id slot status 202.164.42.2 202.164.42.1 QM_IDLE 1 0 ACTIVE Site-1#
The state “QM_IDLE” and status “ACTIVE” means tunnel is up and working fine. If you see “MM_NO_STATE” or anything else under state column, it means there is some issue. You can then use debug ip packet command to check what’s going on the router.
Site-1#show crypto ipsec sa interface: FastEthernet0/1 Crypto map tag: MAP, local addr 202.164.42.1 protected vrf: (none) local ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0) current_peer 202.164.42.2 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 20, #pkts encrypt: 20, #pkts digest: 20 #pkts decaps: 15, #pkts decrypt: 15, #pkts verify: 15 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 5, #recv errors 0 local crypto endpt.: 202.164.42.1, remote crypto endpt.: 202.164.42.2 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/1 current outbound spi: 0xF1C7B7E7(4056397799) inbound esp sas: spi: 0x812DFD73(2167274867) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2001, flow_id: SW:1, crypto map: MAP sa timing: remaining key lifetime (k/sec): (4454151/3381) IV size: 8 bytes replay detection support: Y Status: ACTIVE inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0xF1C7B7E7(4056397799) transform: esp-3des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2002, flow_id: SW:2, crypto map: MAP sa timing: remaining key lifetime (k/sec): (4454151/3378) IV size: 8 bytes replay detection support: Y Status: ACTIVE outbound ah sas: outbound pcp sas: Site-1#
In above output, you can see the complete details of IPsec tunnel.
Now, PC1 and PC2 reach each other which are located on different LAN segments in remote location.
PC1#ping 192.168.10.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.10, timeout is 2 seconds:
.!!!!
Success rate is 90 percent (4/5), round-trip min/avg/max = 1/2/4 ms
PC1#
This concludes our Site-to-Site IPsec VPN Tunnel section.


