- March 26, 2022
- Posted by: Surender Kumar
- Category: PowerShell
Netstat alternate in PowerShell
Table of Contents
The netstat (network statistics) is a really useful command-line tool for system admins when it comes to diagnosing network issues in a system. It shows the protocol-specific networking statistics for each network connection on your computer. People who have been using it for quite some time would surely understand its importance; no matter whether you work in Windows or Linux environment.
In this article, we will discuss the alternative of Netstat in Windows PowerShell. The NetTCPIP module of PowerShell includes Get-NetTCPConnection cmdlet that we can use to get the network statistics like netstat.
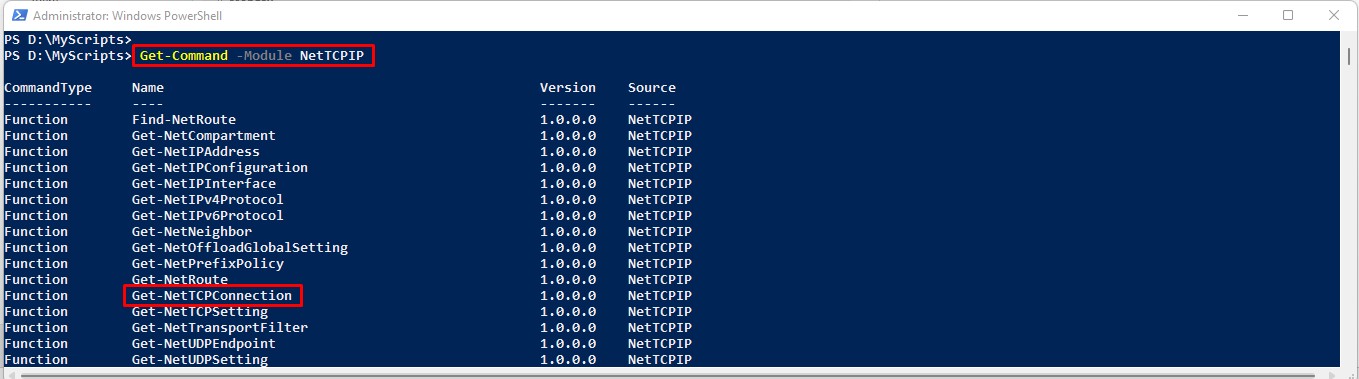
Now lets take a look how to use this command.
Get-NetTCPConnection
If you run Get-NetTCPConnection cmdlet without any parameter, it gives you the following information by default:
- LocalAddress
- LocalPort:
- RemoteAddress
- RemotePort
- State
- AppliedSettings
- OweningProcess
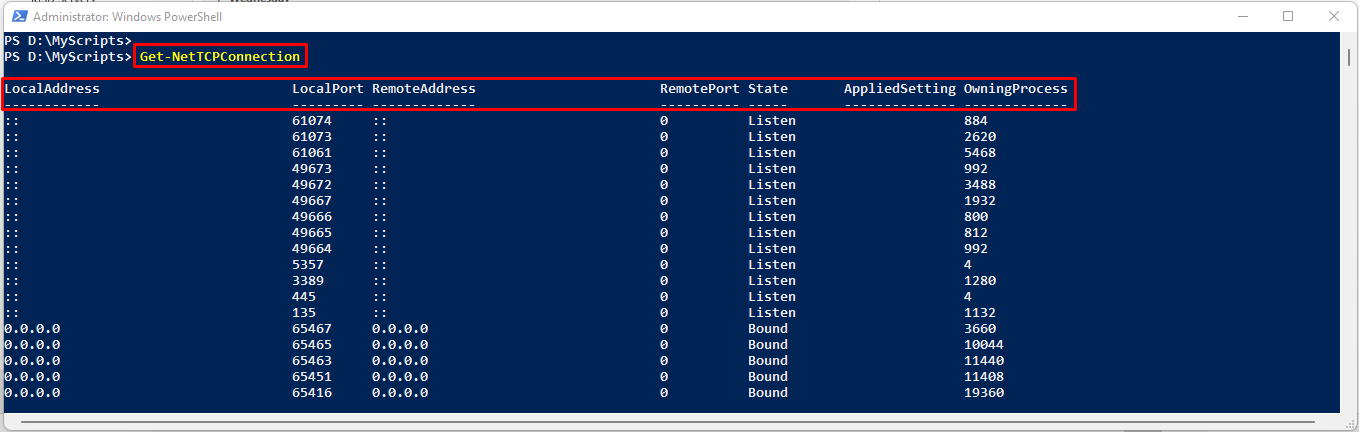
The output of this cmdlet is not exactly the same as that of netstat command but since PowerShell returns objects, we get a lot more control on its output. The above mentioned table headers are not just a text strings; these are the properties that you can use to filter and modify the output of cmdlet.
Filtering the results
By default, the Get-TCPConnection cmdlet returns the stats for all the connections and IP addresses. If you have multiple network interfaces and multiple IP addresses configured in a computer, it will give you too much information which could be overwhelming. To view the stats for a particular network connection in your computer, you could specify the IP address using -LocalAddress parameter as shown below:
Get-NetTCPConnection -LocalAddress 192.168.0.254
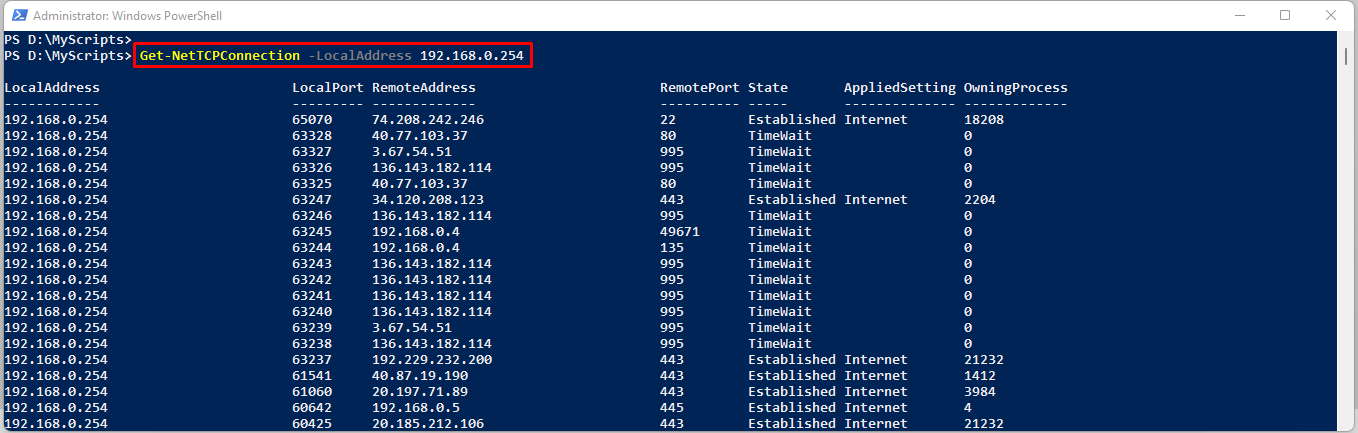
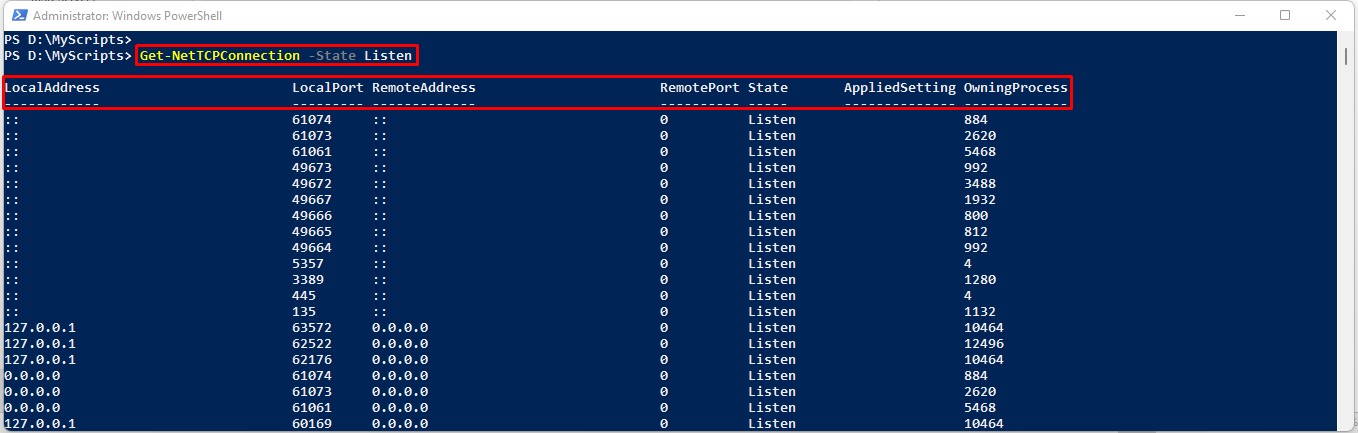
You can filter the results using the properties returned by Get-NetTCPConnection cmdlet. For instance, if you want to only view the connections that are in “Listen” state, you could modify the command as shown below:
Get-NetTCPConnection -State Listen
This command will filter the output and only show the connections that are in Listen state. Have a look at the following image:
You could use this idea to list the TCP ports on your local or remote computers. To do that, you can use the following command:
Get-NetTCPConnection -State Listen | Select Local*, State | sort LocalPort

This command shows all the TCP ports listening on your computer sorted based on local TCP port number. If you’re interested in getting the count of connections that are in ‘Listen’ state, you can use the Measure-Object cmdlet (or measure alias) as shown below:
Get-NetTCPConnection -State Listen | Measure-Object

Similarly, you could combine multiple properties to further narrow down the output and find out the connections that you are interested in particular.
The Out-GridView cmdlet
Instead of using parameters to filter the output of Get-NetTCPConnection cmdlet, you could combine it with Out-GridView cmdlet as shown in the following command:
Get-NetTCPConnection | Out-GridView
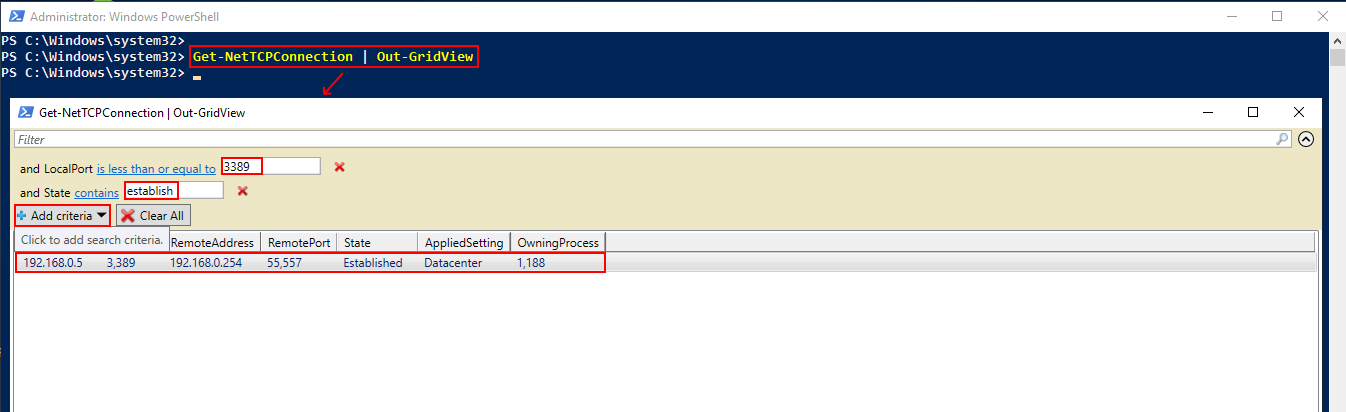
Here, we are getting all the connections with Get-NetTCPConnection cmdlet and passing them to Out-GridView to build a dynamic table. The best thing about this table is that you can add or remove filter criteria by clicking on Add Criteria button and the output will be dynamically filtered in real time as shown in the screenshot.
Check TCP ports on remote server
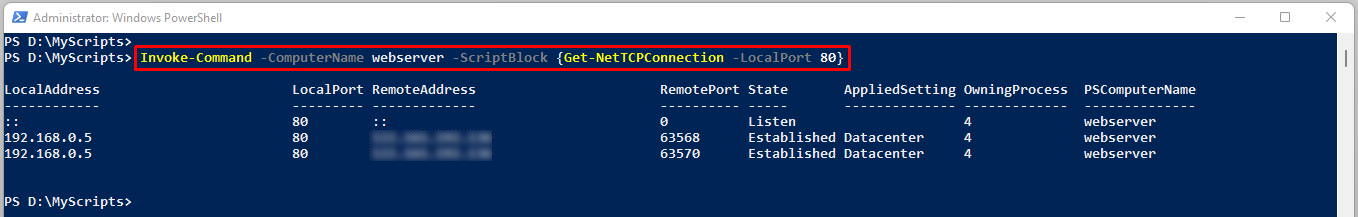
Suppose you’ve a remote web server and you want to find out it is listening on port 80, you won’t even have to login on webserver and launch a command prompt to interactively run netstat or Get-NetTCPConnection command. You could use the PowerShell remoting to run the command from your local computer itself.
Invoke-Command -ComputerName webserver -ScriptBlock {Get-NetTCPConnection -LocalPort 80 | Format-Table -Auto}
Taking it a little bit further, to check if someone is connected to webserver via remote desktop protocol (RDP), you can run the following command:
Invoke-Command -ComputerName webserver -ScriptBlock {Get-NetTCPConnection -LocalPort 3389 -State 'Established'}
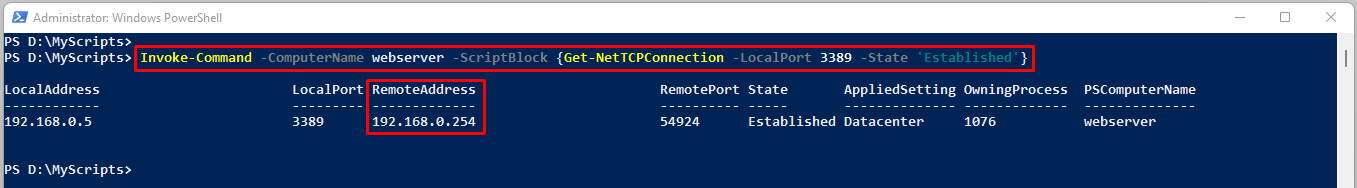
This command shows that someone with IP address 192.168.0.254 is accessing the webserever via RDP.
Determine the name of owning process
Did you notice the OwningProcess column in the output? This property shows the process identifier (PID) of the process responsible for that particular connection. Now you might be thinking it will be a great idea if you could see the process name and executable path in two separate columns. Well, it is possible indeed with PowerShell. See the following command for reference:
Get-NetTCPConnection | select Local*, Remote*, State,`
@{n="ProcessName";e={(Get-Process -Id $_.OwningProcess).ProcessName}},`
@{n="ProcessPath";e={(Get-Process -Id $_.OwningProcess).Path}} | ft -Auto

Take a look at the ProcessName and ProcessPath columns that you just created. The new columns are showing the process name and executable path which is way more useful for admins than just the PID. The above command shows that you don’t have to stick with the default properties of Get-NetTCPConnection cmdlet. PowerShell allows you to build the custom properties (known as calculated properties) on the fly by using other cmdlets.
By the way, you could see the list of all the default properties and methods supported by Get-NetTCPConnection cmdlet using the following command:
Get-NetTCPConnection | Get-Member
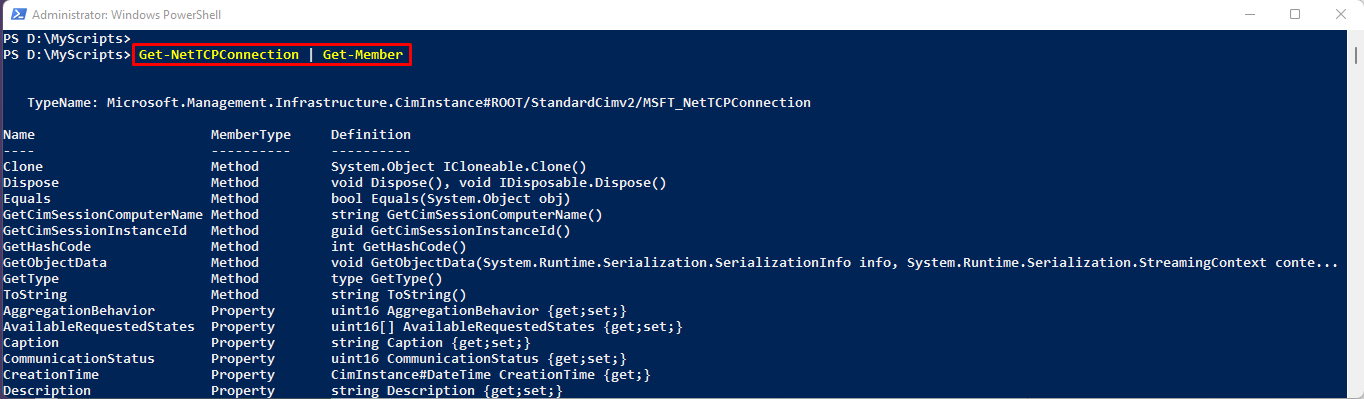
This command shows that there are numerous properties and methods you could use to filter and format the output of cmdlet.
This is just the beginning. Once you start using Get-NetTCPConnection cmdlet, you will discover whole lot of new things that you couldn’t even do with netstat tool. The best thing is that you could even use the netstat (and other cmdline tools) directly in PowerShell so whenever you feel there is something you cannot find in Get-NetTCPConnection cmdlet, feel free to use your old buddy netstat in PowerShell command or script.



The trick to find the process name in the end was really helpful. Thanks for the help.
does Get-NetTCPConnection shows UDP connections?
Is there any way to get RemoteAddress of UDP Connection in powershell? (Get-NetUDPEndpoint doesn’t show RemoteAddress)
UDP is not connection-oriented so you will not see it with Get-NetTCPconnection.
The Get-NetUDPEndpoint cmdlet only shows the local endpoints that your computer is listening on but cannot show remote address due to nature of UDP.